MimbleWimble: History, Technology, and the Mining Industry

Quick Take
- Two privacy-oriented currencies based on the MimbleWimble protocol are pushing out January 2019 launches.
- Both make a number of trade-offs in design decisions, with Grin focusing on a bottom-up “fair launch” and BEAM taking the route of Zcash and other projects in its formal foundation structure.

A historical overview of MimbleWimble, Grin, & BEAM
MimbleWimble, a blockchain protocol focused on fungibility, privacy, and scalability, was released in the wild in July 2016 on IRC channel #bitcoin-wizards by pseudonymous Tom Elvis Jedusor. The paper proposed a novel way of combining transactions to improve the privacy features in a public blockchain.
Jedusor's paper was built on the work of another anonymously posted paper from 2013 using one-way aggregate signatures (OWAS), which required a novel cryptographic primitive, pairing crypto, which wasn't well trusted in academia. It also drew inspiration from Confidential Transactions and CoinJoin, two privacy proposals by Bitcoin Core developer Gregory Maxwell.
The original MimbleWimble paper used the same elliptic curve cryptography Bitcoin uses, catching the attention of many Bitcoin researchers including Andrew Poelstra, a mathematician and applied cryptographer at Blockstream, who further improved on the MimbleWimble white paper, releasing a “precise” version in October 2016. Poelstra's work has long been focused on privacy, having worked on Confidential Transactions and scriptless scripts in Bitcoin.
Originally, it was envisioned that MimbleWimble could either be integrated as an upgrade to Bitcoin or exist as a sidechain, but Pieter Wuille, co-founder of Blockstream and a Bitcoin Core developer, clarified some of the challenges to integrating it as a backwards-compatible change on a 2016 podcast:
"Introducing mimblewimble into bitcoin in a backwards-compatible way would be a difficult exercise. It may not be impossible, but it would be hard. I think the way if people were experimenting with this, I would expect it to be an experimental separate chain or sidechain. In a sidechain we would not introduce a new cryptocurrency but it would be a separate chain. There are some downsides to mimblewimble. In particular, it does not have a scripting language...a scripting language is very neat to play with, but it has a privacy downside. Mimblewimble takes this to the other side where you have very good privacy but at the expense of no other features any more."
The trade-off made by MimbleWimble excludes an expressive scripting language, which allows for innovations such as payment channels (e.g., the Lightning Network) and cross-chain atomic swaps, both of which launched in Bitcoin in 2017. Since then, two separate implementations of the MimbleWimble protocol have emerged, both with different considerations around community, ethos, funding, and technical details.
The first implementation, Grin, which has become synonymous with MimbleWimble, was released just a few days after Poelsta's position paper. Pseudonymous Ignotus Peverell, the original owner of Harry's invisibility cloak, created the Github project ignopeverell/grin, where he provided a partial implementation of the protocol written in Rust, in addition to posting his vision for the project's ethos.
In March 2017, Peverell posted a technical introduction to Grin and MimbleWimble (as the name is now stylized), which serves as the principle reference to the protocol's specification today. To date, the project is still maintained by a group of mostly anonymous developers, several of whom have taken on Harry Potter pseudonyms in line with the original ethos of the project (including Luna Lovegood, Seamus Finnigan, and Percy Weasley). The first Grin testnet was launched in November 2017 and the project is currently on testnet 4, which is believed to be the last before the project's mainnet launch.
The second implementation, BEAM, is a project started in March 2018 and was formally announced on the one year anniversary of the original Mimblewimble paper release. BEAM was presented in a separate white paper (along with a fully functional mining node and wallet client) and took on a more formal structure similar to Zcash, in stark contrast to Grin's anarchic, open-source ethos. The BEAM team is led by CEO Alexander Zaidelson, an Israeli entrepreneur.
With a defined management/engineering team, pre-sale, a formal foundation, and founder's tax, BEAM took a very different approach to present a competitive alternative to Grin in the market. In addition to creating the formal structure around the project, the BEAM team made different technical choices to Grin, including decisions related to the monetary policy and hashing algorithm (which are explored below).
BEAM launched in early January 2019 with a significant lead on hash-rate.
Understanding Bitcoin's UTXO model and cryptographic primitives
Note: This, by no means serves as a comprehensive introduction to Bitcoin or cryptography, but provides enough context such that the uninformed reader should be able to follow along.
From the earliest days, privacy and fungibility have been core concerns of Bitcoin users. Through complex network analysis and blockchain analysis, Bitcoin has seen many attempts to de-anonymize transactions. While cryptocurrencies have emerged where privacy is a top priority (e.g., Monero and Zcash), Bitcoin has also seen significant privacy and fungibility improvements at both the protocol layer and the transaction layer.
Both Grin and BEAM use the same unspent transaction output (UTXO) model that Bitcoin uses, in contrast to other account-based cryptocurrencies such as Ethereum.

A visualization of Bitcoin's UTXO model from Bitcoin.org's documentation.
When 90k satoshis are sent via new transactions TX1 and TX2, two outputs are generated (40k and 50k satoshis respectively) to an address with an amount determined by the sender.
Bitcoin, Grin, and BEAM all allow for this through the use of cryptographic hashing. At a very high-level, a hash function allows you to take an input, apply a cryptographic hash function or CHF (which is a standard transformation) and get a fixed-size output (called a digest). This is illustrated below.
Most importantly: the magic of CHFs represent an asymmetry between an attacker and a defender. What does this mean? It's really easy to hash an input, but really, really hard (impossible in human-time with the world's supercomputers) to reverse a digest to get the original input. This is a good thing: the majority of the world's internet security assumptions, from passwords to public/private keys are hashed and the assumption holds until we have meaningfully powerful quantum computers.
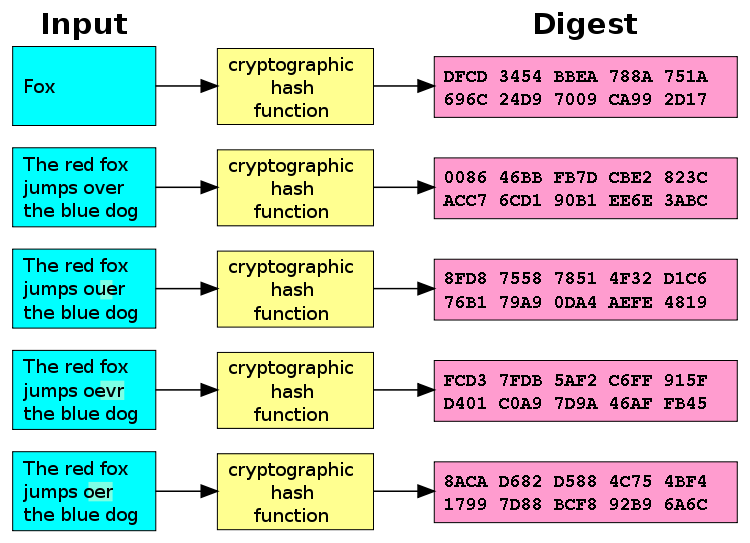
A diagram of a cryptographic hash function. Source: Wikipedia.
In Bitcoin's UTXO model, it's clear there are three pieces of information publicly visible and verifiable: the input information, the output information, and the transaction amount. None of this information is hidden and allows for easy verifiability of how much money is in the system (since all of the UTXOs add up to the expected supply of bitcoins in the system).
However, these properties come with trade-offs: Bitcoin transactions are not very private, since all of this information appears unencrypted to the outside world (though they are hashed). While the community has advanced best practices, such as discouraging address re-use and encouraging the use of "mixers" (where bitcoins are tumbled around with "fresh" UTXOs returned to you), privacy efforts like CoinJoin and Confidential Transactions have been advanced to incorporate more robust privacy features for users.
How MimbleWimble makes privacy improvements
MimbleWimble makes several changes to Bitcoin's UTXO model to enable private transactions, based on Confidential Transactions and CoinJoin. From the documentation:
- There are no addresses.
- There are no amounts.
- 2 transactions, one spending the other, can be merged in a block to form only one, removing all intermediary information.
The first two components are explained by the use of Confidential Transactions, a proposal from former Blockstream CTO (and currently implemented on Blockstream Liquid, a Bitcoin sidechain in production) which uses a cryptographic primitive called a Pederson commitment scheme to improve on Bitcoin's UTXO model. With confidential transactions, only the participants in a transaction can see the transaction amount. In theory, this sounds great, but with one key concern: you need non-participants in the system to be able to tell when a transaction is bogus — to prevent any user from spending more money than they have.
How is this done? A cryptographic commitment sounds fancy, but what it means is, "I am proving I knew something before hashing it because I can't reverse the hash to reveal what I knew." Even outside of cryptocurrencies, commitments are used (for example) by people to prove public predictions, e.g. Nic Carter's public prediction on January 1st about 2018 project development. In 2019, Nic will be able to reveal his list (in plain-text English) and people will be able to easily verify that his list matches (to the character) what was hashed the previous year.
In Bitcoin, where simple cryptographic hash functions are used to make transaction commitments, the input, output, and transaction amounts are all essential. A Pederson commitment improves on this by ensuring that the sum of the inputs and the sum of the outputs are verifiably equal. The cryptographic proofs that allow for this certainty are beyond the scope of this piece, but this reveals one key insight: the specific inputs and output amounts being spent can remain a secret while the security of the system (and verifiability of that security in any given transaction by non-participants) remains intact.
But what's to prevent someone from taking two inputs (e.g., -100BTC, 100BTC), using the 100BTC as an input in a confidential transaction and disregarding the -100BTC? The solution in Confidential Transactions is to use another cryptographic primitive called a range proof. This proof ensures the sanctity of the total supply of money by guaranteeing that the inputs in the system are in a certain range (in this case, positive).
MimbleWimble implementations all use Confidential Transactions to ensure there are no addresses or amounts visible in the system.
The third goal stated above, "removing all intermediary information" is explained by the use of CoinJoin, also created by Gregory Maxwell, and speaks to the transaction graph in a network. While hiding the information explicitly revealed in a transaction is crucial and done with Confidential Transactions, a transaction's history still holds a wealth of implicit information that allows someone with sufficient amounts of computational resources to easily visualize and infer relationships between different transactions in a network. An example of this type of graph is seen below.
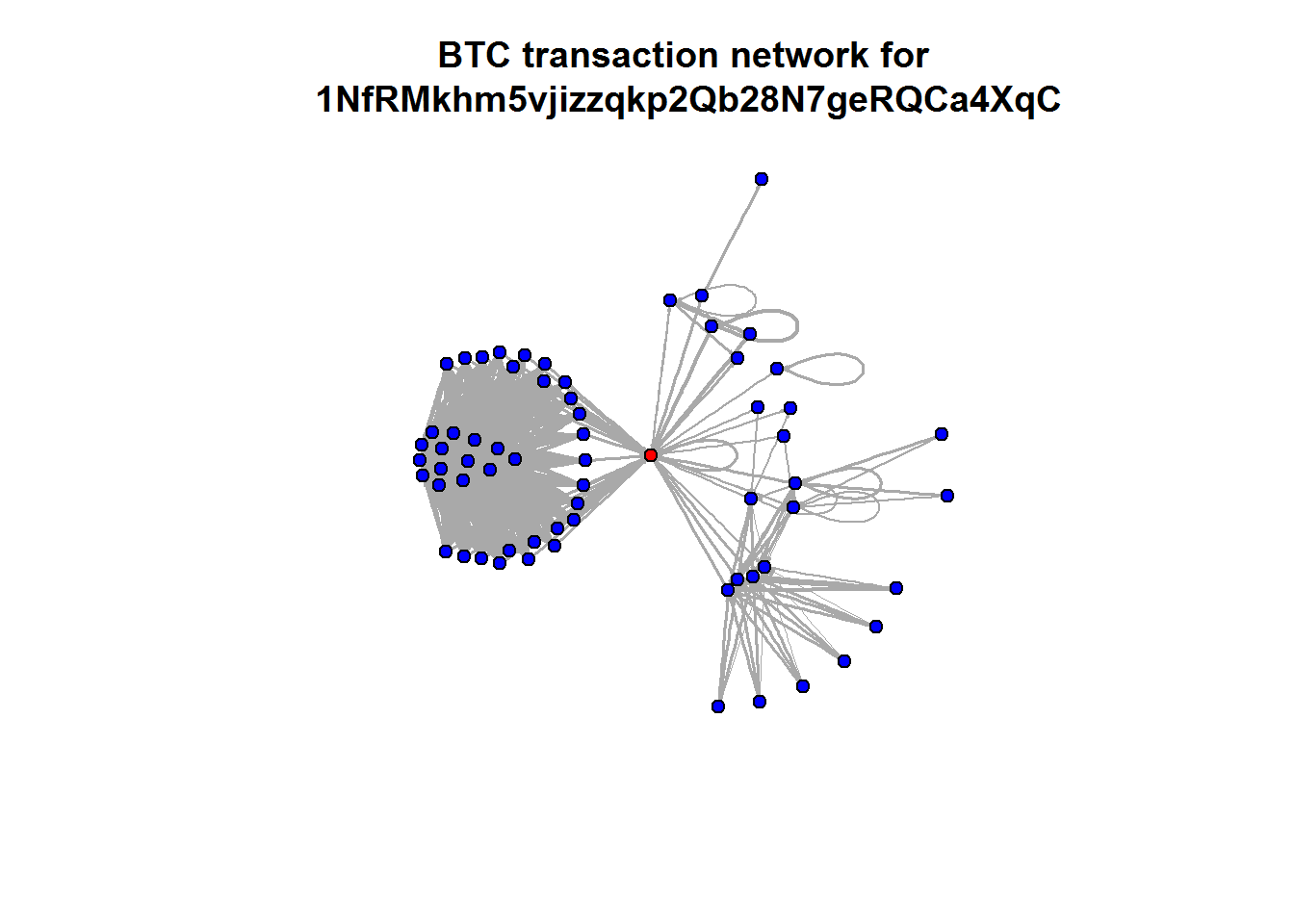
Example of a Bitcoin transaction being visualized, courtesy of Benedict Koehler.
This is not unprecedented — startups such as Elliptic and Chainalysis use these forms of on-chain forensics to detect fraud and "illicit transactions" (e.g., money laundering, black market activity) and are well-funded with users ranging from cryptocurrency exchanges (who use it for compliance) to government organizations. Due to the easy traceability of Bitcoin's network graph, it remains a poor choice for necessarily private transactions.
While presenting a moral argument for the merits of full privacy is beyond the scope of this piece, this problem is not just one for drug dealers and money launderers: an easily traceable network graph allows analysts to make increasingly stronger inferences about transactions on the network over time. Maintaining privacy on this front remains a goal for all proto cyber-monies.
In CoinJoin, inputs from multiple users are combined in what's called an anonymity set and tumbled to ensure that the transaction graph is harder to trace. This is pictured below, where Alice and Bob's 10BTC and 20BTC inputs are combined in a CoinJoin transaction.
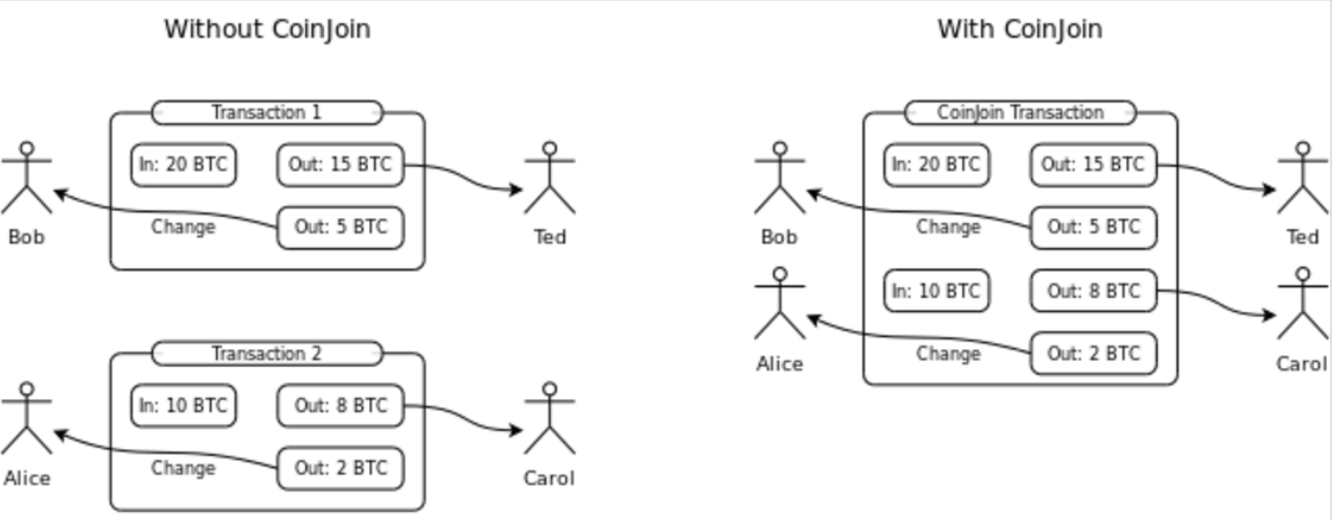
CoinJoin diagram courtesy of Artncase.
Bitcoin wallets such as Wasabi Wallet and tumblers like TumbleBit have implemented CoinJoin to offer transaction-layer privacy for Bitcoin. However, they are unsatisfactory. The anonymity set of these products tends to be very small, with only a few participants in each transaction and tend to take significant time to get matching funds. Researchers have even been able to de-anonymize the majority of transactions in small anonymity sets.
MimbleWimble implementations solve this by making CoinJoin a core part of the protocol, rather than a transaction-layer privacy improvement implemented by third-party wallets and services. In MimbleWimble, all transactions in every block are automatically collapsed into a single transaction and most intermediary transaction information is hidden.
Now you're probably thinking: my inputs, outputs, and transaction amounts are hidden and the transaction graph sufficiently obfuscated... are there any other ways for motivated actors to figure out what I'm doing? The final potential point of failure is in the ability for individual nodes to de-anonymize transactions by leveraging the originating IP address.
When a Bitcoin transaction is made from a wallet, it's broadcast to a set of nodes, which then quickly broadcast to their peer nodes in what's described as Bitcoin's gossip network. Before they're consolidated into a block, because individual transactions are broadcast in pieces, an actor who wants to understand your transactions may do so by recording transactions and the IP addresses they originate from, hoping to use that information to gain information about someone's activity.
The solution to this proposed by MimbleWimble is based on another improvement proposal originally designed for Bitcoin, Dandelion, envisioned by a team of researchers at the University of Illinois at Urbana-Champaign. It has been in discussion since 2017 as a public Bitcoin Improvement Proposal.
The goal of Dandelion is to obfuscate the IP address of a Bitcoin transaction. A dandelion flower's petals have a single stem til they blossom fully. Similarly, with Dandelion, a Bitcoin transaction is broadcast to the network in two phases: the "stem" phase (where it is obfuscated) and the "fluff" phrase where it is broadcast.
First the transaction is broadcast to a single node, which is then relayed to another single peer, until there are enough "hops" from the original peer — at which point, the transaction is broadcast to the rest of the gossip network. A visualization of this can be seen below, where a transaction (in Phase 1) is broadcast to a single peer before spreading to the remainder of the network (Phase 2).

Image courtesy of Giulia Fanti’s presentation "Presenting Dandelion" in Lisbon.
The combination of improvements like confidential transactions, CoinJoin, and Dandelion allow MimbleWimble implementations to do away with traditional ideas like addresses: the commitments made by people generating a transaction serves the purpose of the public/private key used in Bitcoin to conduct a transaction. This allows MimbleWimble to offer material privacy improvements over Bitcoin by offering a fully private cryptocurrency.
The differences between BEAM and Grin
While both Grin and BEAM implement the MimbleWimble protocol from scratch, both come with slight differences:
- The main Grin implementation is written in Rust while the main BEAM implementation is written in C++.
- While both teams are focused on ASIC resistance, they take different approaches in their choice of hashing algorithm and initial approach (explored below).
- The Grin OS team, who has written extensive analyses of the the trade-offs, opted to stick to open-source governance in lieu of a formal foundation. One of the trade-offs is in funding, where Grin subsists on donations. The BEAM team raised a round of private financing in addition to instituting a 20% block reward similar to Zcash.
- In Grin's monetary policy, "a new grin is emitted every second," keeping supply inflation constant forever (though asymptotically approaching 0%). This is motivated by ideological differences to other cryptocurrencies like Bitcoin (which are strongly deflationary at a future equilibrium). Specifically, the Grin team aims to dissuade hoarding of grin. In contrast, BEAM has a fixed supply (of ~263m coins).
- Grin provides a partial-sync mode with several mitigation strategies in case there's an error. This allows nodes to sync to the network with a small fraction of the data necessary for a full node sync (which BEAM requires).
- Beam offers traditional confidential transactions (signed with Bulletproofs). In addition, BEAM has proposed a design for an auditable wallet. The opt-in Audibility feature allows businesses or other users to generate a unique public-private key pair that lets an external third-party verify funds or any meta-data stored in a transaction (e.g. for a document or other digital asset). The Grin team explicitly opted not to extend the implementation beyond core features.
The mining landscape
The mining landscape for both Grin and BEAM remain unclear as both networks are so new (with Grin pre-launch).
The BEAM team opted for modified Equihash PoW (Equihash 150,5 with additional datapath change intended to deter ASICs). This, in addition to a planned six-month hard fork, is intended to deter ASICs from the network.
Grin uses the novel Cuckoo Cycle (to start with), an alternative proof of work system developed by John Tromp in 2015. While the algorithm is intended to be ASIC resistant, the team has long believed ASICs are a potentially inevitability. The solution emerged in September 2018: using two algorithms, one optimized to be ASIC-friendly (Cuckatoo31+) and another to allow GPUs to compete (Cuckaroo29), where the PoW balances mining rewards between the two every 24-hour period.
The GPU of choice among early miners of both Grin and Beam appears to be the Nvidia GTX 1080 TI (which is general purpose hardware also used to mine many other blockchains).
Early BEAM launch stats seem to indicate the dominance of two major pools: sparkpool.com (a multi-asset mining pool with ~69% of the hash rate) and bepool.org (with ~30% of the hash rate) for a total of ~1.5m solutions/sec. The specific number of solutions/sec possible from hardware depends on the miner used (and its optimizations), but with the OpenCL miner clocking ~10 sols/sec and a CUDA-based miner clocking ~15-20 sols, it's likely 100,000+ GPUs are currently securing the network.
The Grin mining market is more institutionalized, with over a dozen private mining operations pitching a wide variety of crypto funds, family offices, and HNW. Individual miners have the choice of joining pools as they launch. The grinmint pool (launched by BlockCypher) and MWGrinPool.com are two options the community has presented.
There are still difficulties in mining so early on: miners for other GPUs (e.g., AMD chipsets) is less accessible, pool software isn't robust or reliable, multi-signature wallet infrastructure doesn't yet exist, and optimizations aren't broadly known to the market. This offers a material information asymmetry to early miners who can leverage technical sophistication. Some companies are aiming to build this infrastructure like 713's grinbox.
Conclusion
In a world with social credit systems and artificial intelligence techniques that are getting increasingly knowledgeable about what you’re transacting, who you’re transacting with, and even what’s going to happen in the future, it’s clear that privacy is important when designing future money systems.
Where even using a privacy method (e.g. a Bitcoin mixer) might otherwise “taint” a user in the eyes of law enforcement, fully private currencies allow users to have plausible deniability over their intentions. While they may have nothing to hide, this is an important distinction.
Grin and BEAM brought two different approaches to the market. Despite surface-level similarities, they differ on virtually every level apart from being MimbleWimble-based. It will take several months, if not longer, for a "winner" to emerge. Though it's unclear which currency will "win," the two launches offer a test of a number of things enthusiasts have always considered supremely important:
- Can immaculate conception launches compete against more formally funded (and perhaps more sustainable) projects, all else (mostly) equal?
- How much does UX (where BEAM appears to have a lead) matter early on v. other factors (e.g. brand, where Grin has advantage)?
- Is it possible for a marginal privacy-oriented cryptocurrency to gain steam, even if novel, in a crowded field (including Zcash, Monero, Bitcoin's own privacy improvements)?
It will be an exciting year ahead for privacy.
Disclosure: Arjun Balaji is an analyst, engineer, and technical advisor to The Block. He founded Shomei Capital and does not have a position in BEAM or Grin (not mining).
Image credit: Shutterstock/Woramet Muangsiri
© 2023 The Block. All Rights Reserved. This article is provided for informational purposes only. It is not offered or intended to be used as legal, tax, investment, financial, or other advice.



