
Why Are Cross-chain Bridges Prime Targets for Hackers & What Can We Do About It

It’s been a difficult year for cross-chain bridges. More than $2 billion in cryptocurrency has now been stolen across 13 different bridge hacks — and most of these thefts have taken place in 2022.

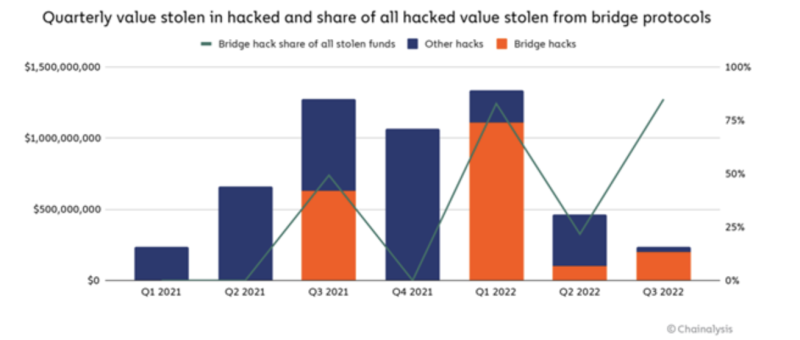
Even more concerning is that cross-chain bridges are now a favored target of North Korean-linked hackers. According to our estimates, the North Korean state-sponsored Lazarus Group has stolen approximately $1 billion in cryptocurrency from bridges and other DeFi protocols so far this year. This is a major threat to the cryptocurrency industry, not to mention national security.
Cross-chain bridges explained
Cross-chain bridges are designed to make blockchains and their tokens interoperable. The wormhole protocol, for example, allows users to move cryptocurrencies and non-fungible tokens between smart contract-enabled blockchains like Solana, Ethereum, and Polygon.
While bridge designs vary, users typically interact with a cross-chain bridge by locking an asset on one blockchain (such as ETH on Ethereum) into the bridge’s smart contract. This triggers the contract to “mint” an asset of equivalent value on another blockchain (such as wETH on Solana). This wETH can always be returned to unlock the original ETH, thereby pegging its value to ETH.
That is, unless the bridge is hacked.
Why are cross-chain bridges so vulnerable?
Bridges are an attractive target because they often centralize their storage of the locked funds that back the “bridged” assets. Regardless of how those funds are secured – with a multisig wallet, a smart contract, or a third-party custodian – that storage center becomes a target.
Secure bridge design is an unresolved technical challenge, meaning that some of the bridges in operation today could still be exploited before best practices are defined.
What the industry can do
While not foolproof, an important first step toward addressing these issues is to make rigorous and recurring smart contract audits a DeFi-wide standard. Developers should coordinate with blockchain security and red teams to test their code before each release. Then, over time, the strongest designs can serve as templates for developers moving forward.
Cryptocurrency services – not just bridges – should also consider investing in security measures and training. For North Korean-linked hackers, for example, social engineering is a favored attack vector, so teams should be taught to recognize the warning signs of a spear phishing attack.
Finally, if a service falls victim to a hack, time is of the essence. Immediately tracing and labeling funds in Chainalysis’s platform can make the difference in preventing bad actors from cashing out the funds they’ve stolen. We recently launched Crypto Incident Response, a rapid response retainer service for cryptocurrency businesses and large organizations that are high-risk targets for cyber attacks, to streamline this very process.
© 2023 The Block. All Rights Reserved. This article is provided for informational purposes only. It is not offered or intended to be used as legal, tax, investment, financial, or other advice.

